
The Death of Website Identity UI & the Rise of Phishing: Why SMS Is Repeating the Same Mistake 🚨
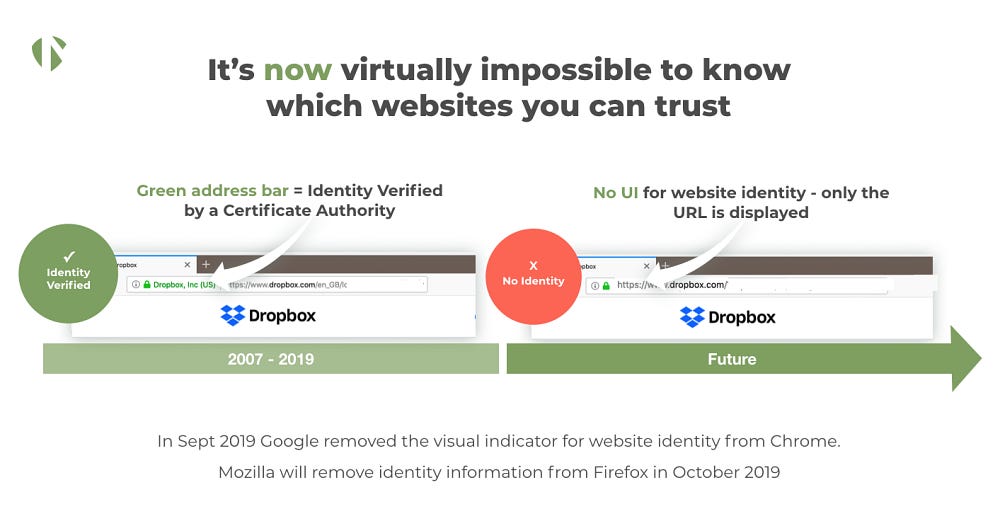
Google and the Death of Website Identity
In 2019, I wrote for the PKI Consortium about how mainstream browsers eliminated website identity indicators — removing a security signal that once helped people distinguish real sites from fakes. The excuse? Most people confused encryption (the padlock) with trust and reputation. Instead of improving the system, browser vendors scrapped it entirely, leaving no simple way to verify legitimacy.

Website identity worked on a basic premise: security vendors verified companies, and browsers displayed that verification for free. It was a visual cue that helped people trust online services. Removing it made phishing easier.
Sender ID Verification: A False Security Promise
A British organization, the Mobile Ecosystem Forum (MEF), introduced sender ID verification for SMS based on a similar model. In theory, it ensures a sender’s identity. In practice, it’s useless.
Operators provide no visual indicator to mobile users. Even if they did, people don’t scrutinize SMS sender IDs the way they check email addresses and domain names. Worse, sender ID verification doesn’t stop criminals from using regular SIM cards for smishing.
💡 The fundamental flaw: There is no way for operators to provide a universal trust indicator for SMS messages. Even if they could, most people wouldn’t notice or rely on it.
Every jurisdiction that has implemented sender ID verification still suffers from rampant smishing. The attack rate hasn’t dropped because criminals simply switch methods. Authentication must happen at the content level — not sender level.
The Only Real Solution 🚀
Maintain sender verification for branding, but shift focus to the real issue: ensuring only trusted web links are delivered.
Sender ID verification doesn’t scale. It’s costly, time-consuming, and ineffective. Mobile networks must authenticate the content itself with a Zero Trust model, treating every link as untrusted until verified. This ensures that even if a message looks legitimate, its embedded links can’t be used for phishing.
Phishing Hasn’t Changed — Defenses Have Failed 🐍
Nearly every major data breach still begins with phishing — just as it did a decade ago. The industry pretends attacks are evolving, but the truth is simpler:
💡 Phishing succeeds not because attackers have improved, but because defenders haven’t.
Security vendors rely on reactive threat intelligence — chasing “known” bad links while criminals register new ones in real-time. Instead of blocking phishing at the infrastructure level, they expect employees and consumers to detect scams on their own.
The worst part? This failure is monetized.
A company built on this flawed model was acquired for $12 billion. Proofpoint, a leader in email and collaboration security, encourages mobile users to report smishing via 7726 — so it can collect data. But they don’t offer a network-level solution to block malicious SMS links in real time. 🤔
🚨 If Proofpoint can filter emails with so-called “advanced AI”, why can’t it do the same for SMS? Because it knows threat-based security fails in real-time. Unlike email, SMS is a public utility. Criminals can test phishing links by sending them to their own phones. If blocked, they swap the link and resend — ensuring only unblocked URLs reach victims.
Microsoft, with $20 billion in annual security revenue, can’t even protect its own customers. In March 2025, Microsoft reported nearly one million devices were compromised via malvertising. If the biggest security companies can’t stop phishing, what does that say about security’s effectiveness?
The Illusion of Progress 🚫
If threat intelligence were actually intelligent, wouldn’t it prevent phishing?
Instead, it’s like a weatherman who only reports rain after you’re already soaked.
Imagine a security guard who tracks every burglary but never locks the door. That’s threat intelligence in a nutshell: a system designed to catalog attacks, not prevent them. Vendors proudly detect breaches — but only after users have been exposed. Few security writers even bother to ask how victims are compromised these days.
Attackers don’t need new techniques or AI-powered malware. They just keep using the same tricks from 1996 because security vendors treat phishing as an identification problem instead of a prevention problem.
🚨 Threat-based security is a whack-a-mole game criminals always win.
Zero Trust for URLs: The Only Real Solution 🛡️
Instead of chasing threats, Zero Trust for URLs verifies only what is safe.
A legitimate website, once verified, remains a known entity. It’s far easier to authenticate PayPal.com once than to chase thousands of new phishing sites impersonating it. Yet, security vendors waste billions trying to detect “bad” links after the fact.
🔑 Verification is a one-time, high-confidence action. Blocklisting phishing sites is an endless, unwinnable war.
Zero Trust SMS: The Only Path Forward for Smishing Defense
Just as website identity should have been improved — not removed — SMS security needs a better model than sender ID verification and reactive firewalls. The only way to stop smishing is to apply Zero Trust at the SMS infrastructure level.
If a link isn’t verified, it should be blocked or replaced with a secure redirect explaining why. This removes the burden from users and prevents phishing before it happens.
🚀 MetaCert has already deployed this model in a live network.
Through a partnership with a European telecom operator, MetaCert has proven that Zero Trust SMS works like a kill switch. Every unverified link is replaced, ensuring phishing attempts never reach a single person. This isn’t a theory — it’s a proven solution, already validated and awaiting regulatory changes before it can be fully activated for mobile subscribers. They informed the GSMA that “it’s the only solution that works”.
💡 Just as we authenticate end-users when they access a login page, we should also authenticate that the login page itself is verified and safe before the user interacts with it.
Meanwhile, the security industry ignores SMS just as browsers ignored website identity verification. The result? Smishing attacks continue to rise.
Phishing Could Have Been Stopped a Decade Ago ⏳
Browsers removed website identity indicators instead of improving them, fueling an explosion of HTTPS-enabled phishing sites.
Now, mobile networks are making the same mistake. Instead of fixing sender ID verification, Ofcom, MEF, and their members pretend it’s effective — while ignoring the only solution that works: Zero Trust for URLs at the network level.
The Bottom Line: It’s Time for Real Innovation 🛠️
Phishing isn’t an AI problem or an awareness problem — it’s an authentication problem. The industry is failing because it keeps trying to identify threats instead of preventing them.
SMS security should follow the same Zero Trust principles used to authenticate the identity of end-users, apps, devices, and network data — to authenticate web links. Authenticate before exposure, not after.
If a URL isn’t verified, it isn’t trusted. It’s that simple.
💡 The security industry’s failure isn’t because phishing is advanced. It’s because security hasn’t evolved.
